scdbg findsc modeAuthor: David Zimmer Date: 02.19.11 - 9:05am Wrote a routine to locate shellcode in a binary file the other day. It can be accessed with the -findsc option in scdbg. It is basically a step count brute forcer which will try to start execution at each offset and log results. For each start position that shows promise, the offset, step count and first 10 opcodes are displayed. At the end the user is asked where to start execution at. The core logic is shown below: 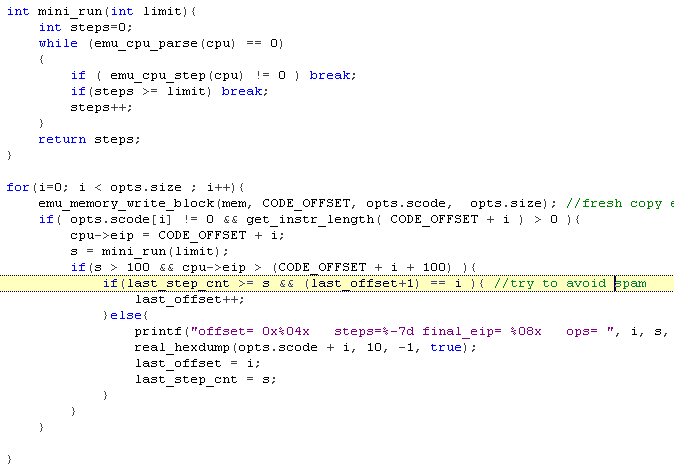
I took 18 of my shellcode samples, appended random amounts of garbage to the beginning, and then ran them through this routine. There was only one that it couldnt find a valid start address for. It has proven to be a useful compliment to the libemu -getpc mode. After a little more testing, I should be able to have it just auto select the highest step count and go from there, for now though the extra information is useful. Will also need to do more testing on more complex files such as malicious Office documents. (although the signature based approach that Office MalScan takes is probably better for files which are likley at least several hundred kb in size) Comments: (1)On 02.23.11 - 12:17am Dave wrote:
|
About Me More Blogs Main Site
|
||||||||||||||||||||||||||||||||||||