
Note: Due to AV detections, this is now its own download: Source & Binary
This research application was designed to allow malcode analysts to quickly get an overview of an unknown shellcodes functionality by actually executing it within the framework of a minimal sandbox implemented through the use of API hooking.
It is not recommended to run unknown payloads outside of VMWare type enviroments. By using this tool, you take responsibility for any results the use of this tool may cause. It is NOT guaranteed to be safe.
Several sample shellcode payloads are provided (*.sc) in the applications home directory.
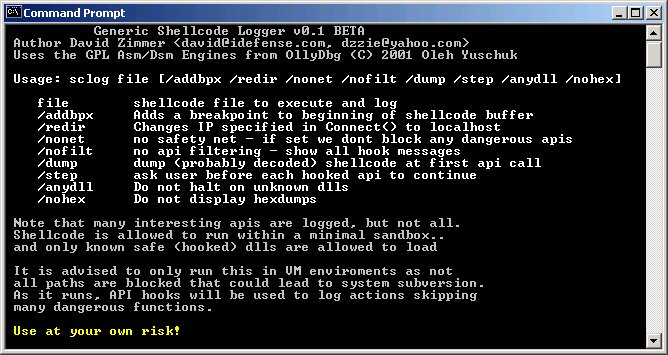
Actual run log of program with recv_file.sc sample:
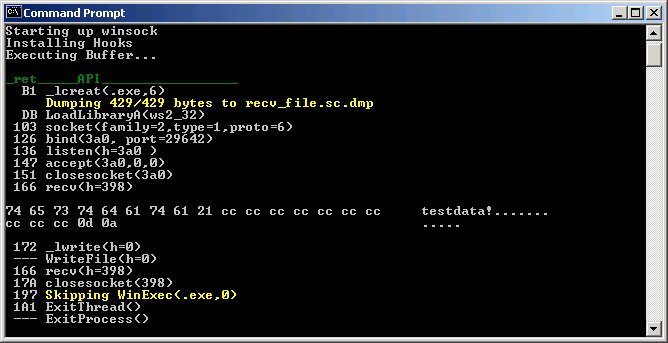
Note:
return addresses shown are relative the relative shellcode offset If you use /dump option to get decoded opcodes, these offsets will be directly after the call that lead to the API call.
A "---" in return address field, means the api was called from outside of the shellcode buffer.
No entry in this field denotes a sc_log generated info msg (yellow)